CCNA Security
CCNA [Cisco Certified Network Associate] [Download Outline] CCNA Security Course Contents Outline Building a Simple Network Establish...

Enrolled
2894
Investment
20,000
Course Overview
Everything you need to know about this comprehensive Meta marketing course
CCNA [Cisco Certified Network Associate]
CCNA Security Course Contents
Outline
- Building a Simple Network
- Establishing Internet Connectivity
- Managing Network Device Security
- Introducing IPv6 Building a Medium-Sized Network
- Troubleshooting Basic Connectivity Wide Area Networks
- Implementing an EIGRP-Based Solution
- Implementing a Scalable OSPF-Based Solution Network Device Management
Describe common security threats
- Common threats to the physical installation
- Mitigation methods for common network attacks
- Email-based threats
- Web-based attacks
- Mitigation methods for Worm, Virus, and Trojan Horse attacks
- Phases of a secure network lifecycle
- Security needs of a typical enterprise with a comprehensive security policy
- Mobile/remote security
- DLP
Security and Cisco Routers
Implement Security on Cisco routers
- CCP Security Audit feature
- CCP One-Step Lockdown feature
- Secure router access using strong encrypted passwords, and using IOS login enhancements, IPV6 security
- Multiple privilege levels
- Role-Based CLI
- Cisco IOS image and configuration files
Describe securing the control, data and management plane
Describe CSM
Describe IPv4 to IPv6 transition
- Reasons for IPv6
- Understanding IPv6 addressing
- Assigning IPv6 addresses
- Routing considerations for IPv6
AAA on Cisco Devices
Implement authentication, authorization, and accounting (AAA)
- 8.1.a AAA using CCP on routers
- 8.1.b AAA using CLI on routers and switches
- AAA on ASA
Describe TACACS+
Describe RADIUS
Describe AAA
- Authentication
- Authorization
- Accounting
Verify AAA functionality
IOS ACLs
Describe standard, extended, and named IP IOS ACLs to filter packets
- IPv4
- IPv6
- Object groups
- ACL operations
- Types of ACLs (dynamic, reflexive, time-based ACLs)
- ACL wild card masking
- Standard ACLs
- Extended ACLs
- Named ACLs
- VLSM
Describe considerations when building ACLs
- Sequencing of ACEs
- Modification of ACEs
Implement IP ACLs to mitigate threats in a network
- Filter IP traffic
- SNMP
- DDoS attacks
- CLI
- CCP
- IP ACLs to prevent IP spoofing
- VACLs
Secure Network Management and Reporting
Describe secure network management
- In-band
- Out of band
- Management protocols
- Management enclave
- Management plane
Implement secure network management
- SSH
- syslog
- SNMP
- NTP
- SCP
- CLI
- CCP
- SSL
Common Layer 2 Attacks
Describe Layer 2 security using Cisco switches
- STP attacks
- ARP spoofing
- MAC spoofing
- CAM overflows
- CDP/LLDP
Describe VLAN Security
- Voice VLAN
- PVLAN
- VLAN hopping
- Native VLAN
Implement VLANs and trunking
- VLAN definition
- Grouping functions into VLANs
- Considering traffic source to destination paths
- Trunking
- Native VLAN
- VLAN trunking protocols
- Inter-VLAN routing
Implement Spanning Tree
- Potential issues with redundant switch topologies
- STP operations
- Resolving issues with STP
Cisco Firewall Technologies
Describe operational strengths and weaknesses of the different firewall technologies
- Proxy firewalls
- Packet and stateful packet
- Application firewall
- Personal firewall
Describe stateful firewalls
- Operations
- Function of the state table
Describe the types of NAT used in firewall technologies
- Static
- Dynamic
- PAT
Implement Zone Based Firewall using CCP
- Zone to zone
- Self zone
Implement the Cisco Adaptive Security Appliance (ASA)
- NAT
- ACL
- Default MPF
- Cisco ASA sec level
Implement NAT and PAT
- Functions of NAT, PAT, and NAT Overload
- Translating inside source addresses
- 7.6.c Overloading Inside global addresses
Cisco IPS
Describe IPS deployment considerations
- SPAN
- IPS product portfolio
- Placement
- Caveats
Describe IPS technologies
- Attack responses
- Monitoring options
- Syslog
- SDEE
- Signature engines
- Signatures
- Global correlation and SIO
- Network-based
- Host-based
Configure Cisco IOS IPS using CCP
- Logging
- Signatures
VPN Technologies
Describe the different methods used in cryptography
- Symmetric
- Asymmetric
- HMAC
- Message digest
- PKI
Describe VPN technologies
- IPsec
- SSL
Describe the building blocks of IPSec
- IKE
- ESP
- AH
- Tunnel mode
- Transport mode
Implement an IOS IPSec site-to-site VPN with pre-shared key authentication
- CCP
- CLI
Verify VPN operations
Implement SSL VPN using ASA device manager
- Clientless
- AnyConnect
Practical Approach
- A real-time examples will be given throughout the lectures, starting from design, analysis, implementation and maintenance of network.
www.ict-trainings.com/curriculum/ccna-security-leaflet.pdf
What you will learn
- ✔ Develop a strong understanding of core concepts and best practices
- ✔ Apply theoretical knowledge to real-world projects
- ✔ Build practical skills through hands-on exercises
- ✔ Improve problem-solving and critical-thinking abilities
- ✔ Learn to plan, execute, and optimize projects effectively
- ✔ Communicate ideas and strategies clearly and professionally
- ✔ Use industry-standard tools and techniques confidently
- ✔ Manage time and resources efficiently to meet deadlines
- ✔ Work collaboratively and adapt to team environments
- ✔ Analyze performance and implement data-driven improvements
- ✔ Gain confidence to apply your learning in a professional setting
- ✔ Prepare for advanced learning or career opportunities in the field
Reviews
No reviews yet. Be the first to review this course!
You must be logged in to submit a review.
Login to ReviewBook Online
Frequently Asked Questions
Find quick solutions to common queries and get the most out of your learning experience
View More QuestionsRelated Courses
Courses that help building your career

Generative AIs
Generative AI This is career-oriented training for you, after completion ...

Prompt Engineering
Prompt Engineering Duration: 4 Weeks Level: Beginner → Intermediate Fo...

AI Engineer track
AI Engineer Track It's a complete roadmap for anyone who want to start earning...

Build Android Apps with AI
Getting Started with Android App Development Introduction to Android apps and Androi...

Python Developer Track
Python Developer Track It's a complete roadmap for anyone who want to sta...
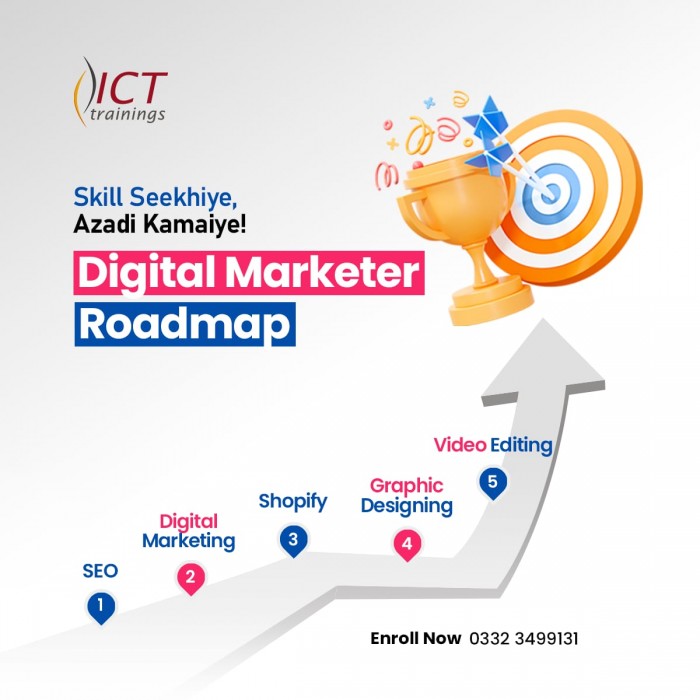
Digital Marketer Track
Digital Marketer Track It's a complete roadmap for anyone who want to start ea...
